Introduction to Firewalls
One of the most overlooked yet important aspects of cryptocurrency is securing personal funds. Even if an individual leaves their cryptocurrency on centralized exchanges they could become compromised and risk losing their funds from being hacked. In a previous post, we covered the importance of browser security.
This article will focus its attention on building a very basic firewall.
A static firewall blocks ports. Ports are doors that are open to the internet. When a computer does not have a firewall all doors are open by default which leads to various ways to become compromised. There are several types of firewalls. The two major categories are static vs dynamic and software vs hardware.
Static firewalls simply look at a packet coming or going out of an internet connection, determine what port it’s coming from, and block or allow that connection. Other functions these types of firewalls can do include logging; blocking IP addresses; closing and opening ports; and other types of useful rules. In this tutorial we will make the simplest firewall possible that blocks all ports by default and only allows the select few we need to navigate the internet.
Dynamic firewalls are more complex and filter different information packages. Their rule sets are dynamic, which means that they can be set to warn users of suspicious behavior and let the administrator take action. They can also be used to filter out malware, do deep packet inspections, and other useful tasks. They are much more advanced and harder to configure.
Software-type firewalls exist directly on a computer. This means that the router network is completely open but the computer is not. This is essentially the last line of defense before an unwanted intruder breaks into a computer. Hardware firewalls on the other hand exist on a router. This means that the home network is secured. In other words, all computers connected to that particular internet connection are protected by the firewall no matter the device.
Firewall layering occurs when multiple firewalls are placed on top of one another. This means that it is possible to have a router that dynamically filters out packets and sniffs for suspicious behaviour while, for example, a static software firewall blocks all the unnecessary connections by default (ie: closes all the unwanted doors that are opened). The more complex the system the harder it is to get into. By the same token however, the harder it is to set-up. As we will soon see however a simple firewall is relatively easy to set up. This tutorial covers how to set up a firewall on either a windows or Linux environment.
Configuring a firewall on linux:
There are two ways to configure a firewall on Linux, Uncomplicated FireWall (ufw) or IPTables. To make things as simple as possible we will be using UFW. IPTables has more rule sets and options but this tutorial is simply a beginner’s guide to get someone started. Most Linux distros include UFW straight out of the box, but just in case make sure it is installed via your package manager. Depending on the distribution being used, package managers and commands will differ. Once UFW is confirmed as installed there are two methods: using a graphic user interface or using the command line.
Using the command line is easy with UFW because there are very few commands, however this tutorial assumes that the user starts sweating buckets every time the terminal is mentioned, so we will only cover the GUI. As we can see, the user interface is very straight forward. When setting the firewall, make sure to allow everything at the beginning and gradually add in new rules while setting up the firewall. This is simply best practice.
Once the firewall rules are set make sure to deny all incoming traffic by default as indicated below. This is because we assume that all traffic exiting our computers is safe, while anything coming into our computers is potentially malicious.
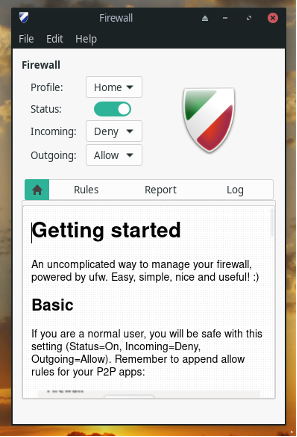
The simplest possible firewall that an individual can make is by opening the following ports:
port 443: HTTPS
port 80: HTTP
port 53: DNS
port 587: SMTP (aka email)
port 9050: access to the TOR network (though not necessary this is a fairly notable one)
If you were to enter in the terminal sudo ufw status the output should look something like this:
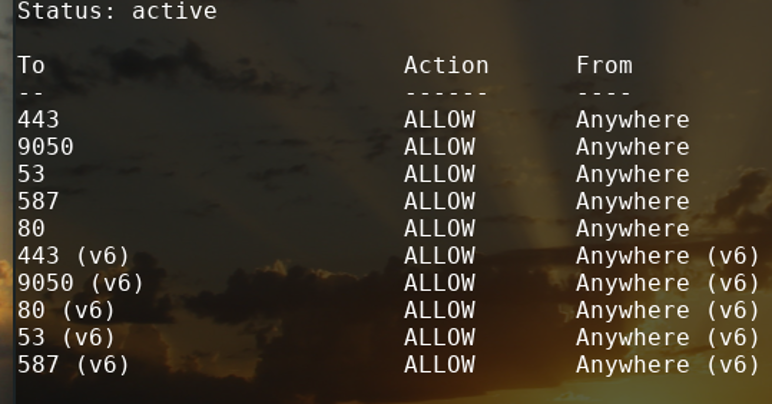
By clicking on rules and then the plus sign at the bottom left of the GUI, you will see this interface. Most protocols covered in this tutorial use TCP connection.
For more information on ports and their numbers feel free to use the following two websites:
https://howdoesinternetwork.com/2012/tcp-udp-port-numbers-list
https://www.speedguide.net/ports.php
Keep in mind that certain internet services use different port numbers. Protocols like SQL (118), IRC (194), SSH (22), and others exist which have specific ports that need to be opened up. Do your own research.
Once all the rules are added, deny all incoming access and there you have it! Your firewall is in place. If your Linux operating system has systemd (normally they do) then you can write down the following command in the terminal to have the firewall to activate automatically on start-up: sudo systemctl enable ufw.
Configuring a Firewall on Windows:
For people using Windows users can go to Control panel > All control panel Items > Windows Firewall and turn on the firewall from there either with simple rules (private networks) or more robust ones (public networks). It’s possible to disable or enable what applications that can connect to the internet via the “allowed apps” section. Under advanced settings it’s possible to create a personalized ruleset like the one mentioned above under the Linux section of this tutorial.
Conclusion:
At the end of the day, a system is only as robust as you make it. If you want the system to be more secure it’s possible to remove port 80. This will mean that all http requests will be automatically denied. This is very powerful because it ensures you do not access websites without a secure connection.
In a previous article we mentioned HTTPS Everywhere as a potential firefox add-on. Using a firewall instead is arguably more robust. Be careful however because blocking port 80 could lead to breaking websites you are looking to access on a main computer. If this computer is used solely for cryptocurrency transactions, it might be a good idea to keep it shut. Adding the Ipv6 versions of the ports might be a good idea as well for slower internet connection.
As always, do your own due diligence. This is a good starting point on firewalls however there is a lot more information to go through. This type of firewall will be reasonably secure however this is merely the starting point. Just like a locksmith or theif can pick a lock, it’s far better to have the door to your house locked then to have it completely opened up.