Virtual Private Networks (VPNs) are networks that bounce your internet traffic through a server in a different location than your own using an encrypted client and server. This means that users access the internet from a different place in the world after the traffic has been routed through a different server. As we will see, this means better network security among other benefits.
VPN vs ISP:
A VPN hides your IP address by redirecting the network traffic through a remote server secured by encryption run by a host. This is practical because unencrypted data can be viewed by anyone who has network access and wants to see it. With a VPN, hackers, governments (which can be the biggest hackers of them all), multinational corporations, cybercriminals, and other parties can’t decipher this data. Keep in mind though that if a VPN logs data they potentially have access to all this information. A user is less susceptible to getting their information leaked by outside actors, but they need to trust the server they are running the VPN on. So the question is: Who do you trust more, the ISP (Internet Service Provider) or the VPN you are using? VPNs are more trustworthy because your ISP does not encrypt the information, logs it, and allows everyone to see it. For those same reasons, it is important to do your own research when picking one.
Your ISP may seem
trustworthy, but it shares your browsing history with advertisers, the police
or government, and other third parties. ISPs can also fall victim to attacks by
cybercriminals: If they are hacked, your personal and private data can be
compromised. Your ISP usually sets up your connection when you connect to the
internet. It tracks you via an IP address.
Security concerns
are especially an issue if a user is connecting to public Wi-Fi networks (even
more so with a cellphone). Anyone can run a package sniffer and monitor
internet traffic. All information that is used can be stolen from a user.
Passwords, personal data, payment information, etc. are not safe. Routing your
device’s internet connection through your chosen VPNs private server rather
than your internet service provider (ISP) changes a user’s IP address so there is
less risk. It also makes it more difficult for those types of tools to see what
you are doing since your information is routed to a different source.
Therefore, a hacker needs to use other means to access a user’s device
information.
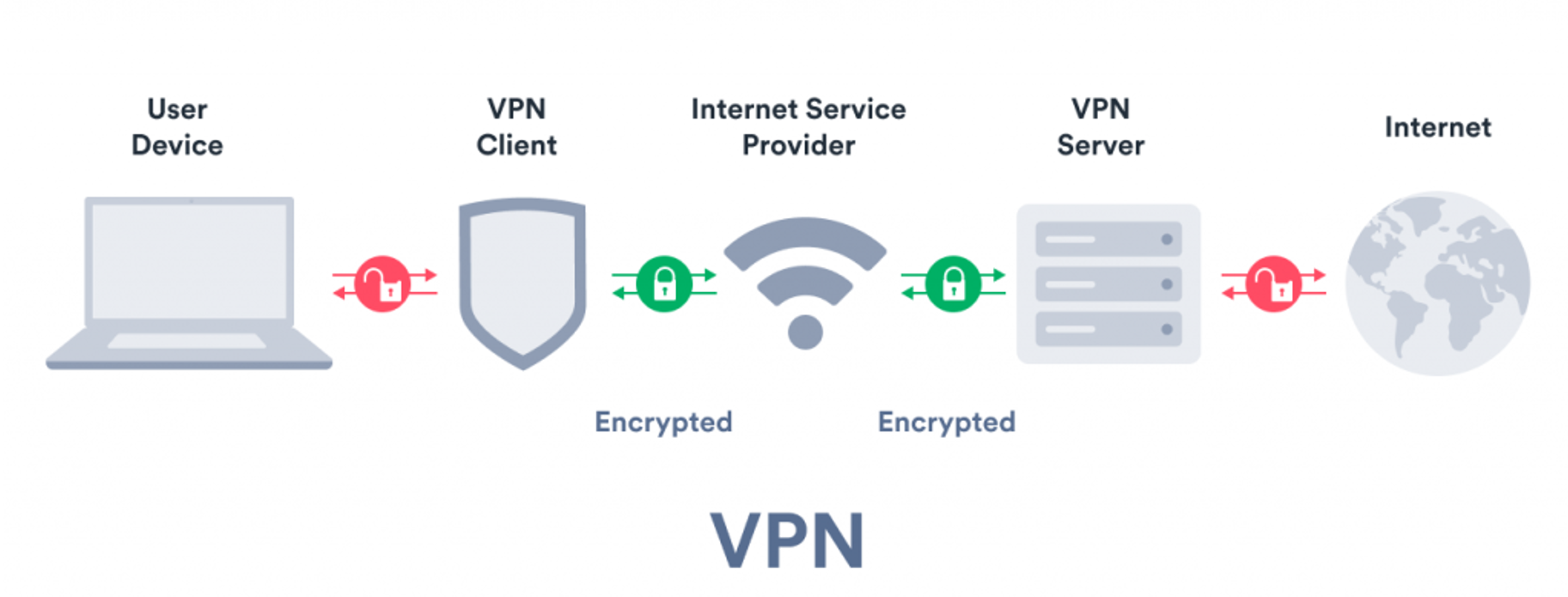
Virtual Private Networks
The VPN server
becomes the source of your data that is used to access services online. This hides
sent and received data and visited websites from your Internet Service Provider
(ISP). It masks an IP address from the ISP by shifting it to a different place
of origin based on the chosen country, hiding your location from malicious
actors through an encrypted tunnel. The VPN forwards the request to access the website
and sends back the response through the secure connection. This makes the
encryption end-to-end which means that man-in-the-middle attacks cannot be
performed unless the actor is connected to the same tunnel as you are. Because
VPNs use a dedicated tunneling system for each user or with every new
connection, this makes it near impossible to get into it.
VPNs run servers and make data readable to the user with encryption keys. A private key is used to access the initial tunnel and fetch information while public keys allow a user to connect and access the data on the internet. This functions much the same way as a cryptocurrency wallet does, but is used as a method to sign users in a VPN tunnel.
 Source: https://surfshark.com/learn/what-is-vpn
Source: https://surfshark.com/learn/what-is-vpn
A VPN enables a variety of protections including: protect and hide a user against IP address leaks, encrypt internet traffic, access information and websites restricted by local governments, protect from location leaks, protection against trackers who trace browsing habits, encrypt traffic, and reduce targeted advertising. It does not protect your email; credit card information when purchasing; Google or Facebook trackers if you are using their services or browsing while signed on to them; and all social media information and other information you post online. Depending on how it is set up (in most cases) it will not protect you against your ISP knowing the information you are downloading or torrenting. This is because while you are downloading you are exposing your host IP address in order for the information to be transferred to your computer. It also protects against leaving information about a user’s internet history, search history and cookies. Cookies can display certain information about a user such as personal data, financial information and other content on websites. A good VPN also has a killswitch which can detect downtime and terminate programs, to reduce (possible) data that could be compromised. It also enables two-factor authentication so that third parties cannot log in on your behalf or access your connection.
VPNs hide internet proxies which hide a user’s location. Furthermore, most VPN services do not store logs of your activities. Some providers track and log data but allegedly do not pass this information on to third parties. This means that any record of the user behavior remains hidden (supposedly – remember that this information could be accessed at any time). Make sure to look at VPN guidelines before signing up for one. Be careful though as such VPN service providers, especially those with large market campaigns and advertising, are not reliable because they’ve previously given information when they were requested to, or outright lie about their practices proven by using package sniffing tools among other ways to identify what is going on with the network a user is connected to.
Conclusion
A VPN connection re-routes and encrypts a user’s IP address through a tunnel. This disguises your IP address when you use the internet. A VPN connection is also secure against external attacks. That’s because only you can access the data in the encrypted tunnel – and nobody else can because they don’t have the key. A VPN allows you to access regionally restricted content from anywhere in the world. Many streaming platforms are not available in every country. However, remember that only your data traffic on the internet is anonymized and protected by using a VPN. The VPN connection does not protect you from other forms of attack or if your device is already compromised in some way shape or form.
Last but not least, do your research and be careful of VPNs who have a history of logging data, giving data to governments, and other things of that nature. Do not assume you are safe on the internet because you are using a VPN.