Securing a browser is an important step to properly protecting a computer from tracking, malware, spyware, pop-ups, ads, and a whole host of other potential security vulnerabilities while browsing the web. Our first task however is to identify what purposes a hardened browser would be of importance. For the average user there are many, but in particular people who use cryptocurrency and manipulate them on centralized exchanges should have a suite of tools that use proper operational security measures. One of them is browser security.
Firefox will be the only web browser that will be covered in this tutorial, because it is built with this type of concern in mind, making it the best browser to “harden.” Recently, we gave a short review of the Brave browser while covering the Basic Attention Token in our Fundamental Analysis report. To surmise, Chrome and chromium-based browsers do not offer the same amount of tools and typically do not have adequate configuration settings to perform this task to the degree it should be practiced while handling cryptocurrencies on a browser.
Over the course of several years the authors of this article have used many different tools and add-ons, generally migrating between different options to identify what works best together. Some of the content may have personal biases due to personal experience between different add-ons. Some add-ons may not be covered but do exist. As always, do your own research on the matter and come to your own conclusions. This beginner’s guide is more along the lines of a resource that points to different directions, and we may develop some of those in-depth in the future.
Part One: General settings on a hardened browser
Up at the top-right hand side of Firefox are three bars. Click on that followed by settings. Configure your browser as you see fit under general, home, and search. For your search engine you can use searx.run, a website that requests links from different search engines for you so you don’t have to go directly on to them. They also have many configuration tools and settings depending on what you are looking for. Depending on the add-ons you decide to use there could be conflicts so be sure to run some tests with it. Other than that, duckduckgo.com is the next best option.
Under Privacy and security, you will find Enhanced Privacy Tracking protection and change the settings to what is more or less shown below. It’s pretty self explanitory.
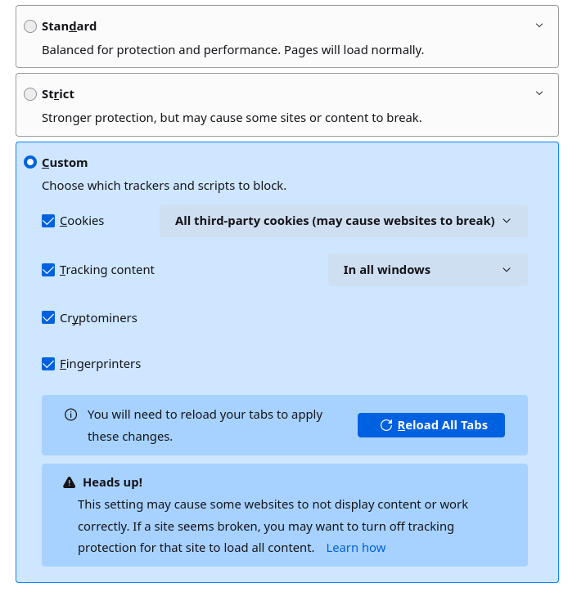
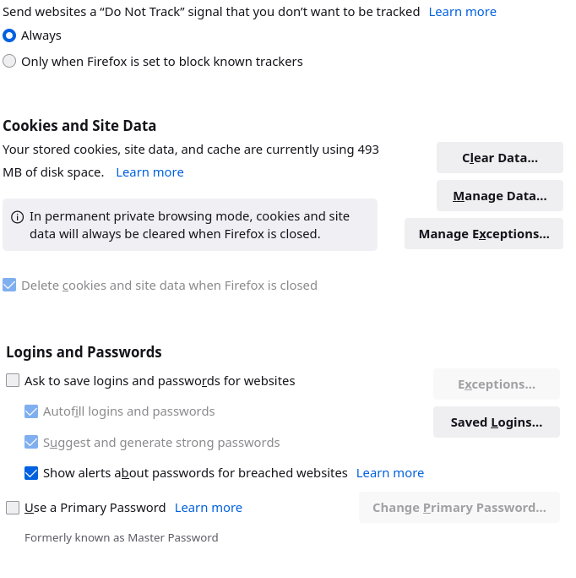
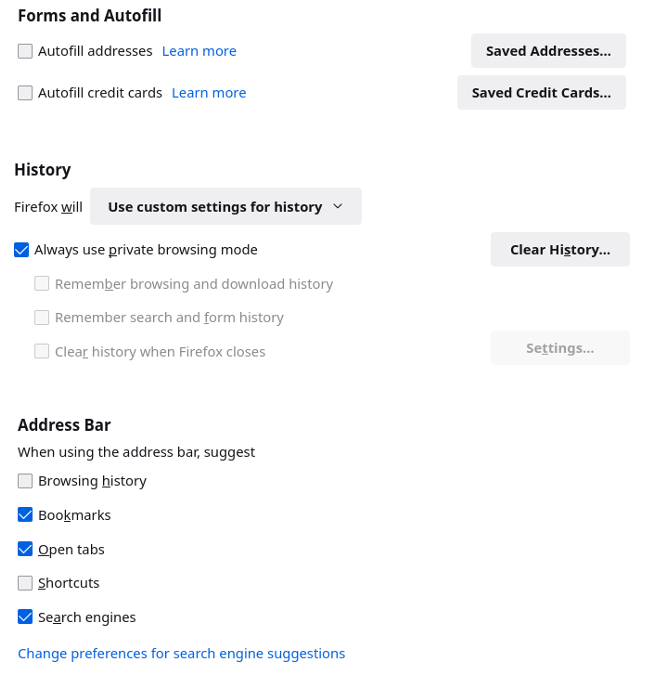
As everyone can see this is permanently set in private browsing mode. Of course private browsing isn’t private, but at least it clears all history once the browser is closed. We’ve configured private browsing to host bookmarks which can lead to certain trackers detecting this browser.
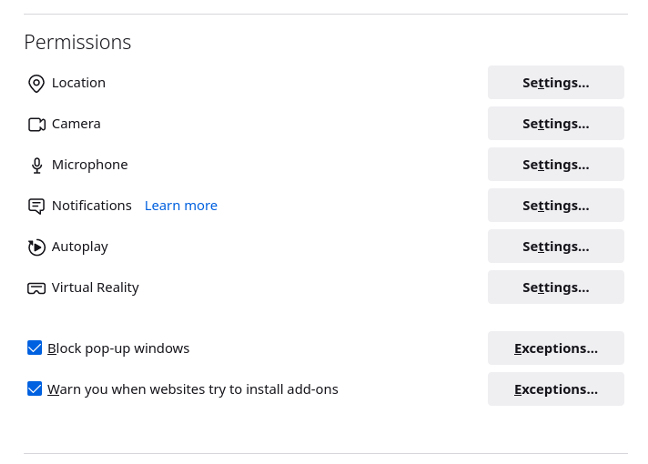
Under the Permissions section you can also block all microphone, location, web camera, and other requests. As always it depends on your level of security and what you want to accomplish.
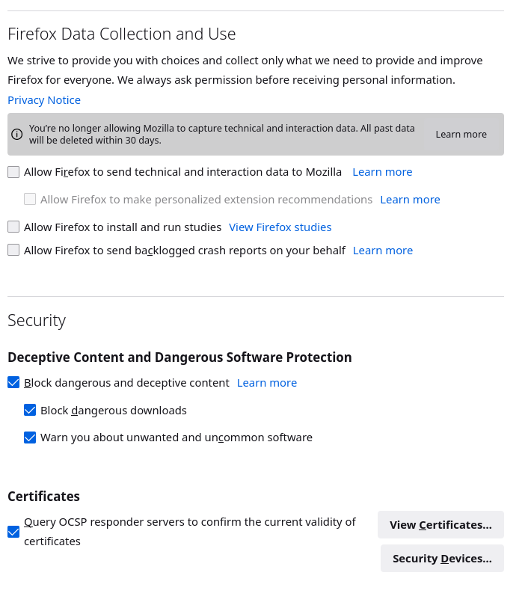
And don’t forget to enable HTTPS-only mode at the end. Be warned you will start to break some less security-oriented sites once you’ve made these changes.
Part Two: Add-ons
One of the simpler solutions to hardening your browser is to install a few add-ons. These tools help eliminate certain vulnerabilities and exploits through various methods. The issue come when an individual has too many add-ons. The more add-ons, the bigger your signature becomes and the more identifiable the browser becomes. This is why it is recommended to use multiple types of browsers for various tasks. Using a combination of them means it is harder to track because of the various browser fingerprints you use. Below is a site created by the Electronic Frontier Foundation (an organization committed to spreading information about tracking and tracing online) that can be used to test your browser fingerprint uniqueness. Keep in mind that some of the tools discussed may conflict with each other or have redundancies (i.e. two programs providing the same type of utility). Browser fingerprinting means that it is important to be cautious about what is being installed along with the configuration settings that the user decides to implement.
https://coveryourtracks.eff.org/
HTTPS Everywhere was created by the Electronic Frontier Foundation. It blocks HTTP requests, which we don’t want. These types of requests can be used to inject malware, track your internet habits, redirect you to malicious websites that mimic those you are trying to access, among other risks.
https://www.eff.org/https-everywhere
Add Blockers come and go, but one of the most popular options is uBlock Origin.
https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
Clearing and blocking trackers is always fun. I like to use a combination of them: ClearURLS, Decentralize, cookie autodelete, and canvas blocker are all good tools that can perform components of these tasks. As always when using a combination of add-ons be sure to test and research to see if they are redundant or incompatible with each other.
https://addons.mozilla.org/en-US/firefox/addon/clearurls/
https://addons.mozilla.org/en-US/firefox/addon/decentraleyes/
https://addons.mozilla.org/en-US/firefox/addon/cookie-autodelete/
https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/
Two of the best script blockers are uMatrix, which is good for blocking a whole host of different websites, third parties, and many others (it is more advanced to configure so be warned), and NoScript, which still remains the best add-on to disable Javascript in the authors’ opinion. It performs much the same function as uMatrix but is more user-friendly.
https://addons.mozilla.org/en-US/firefox/addon/noscript/
https://addons.mozilla.org/en-US/firefox/addon/umatrix/?utm_source=addons.mozilla.org&utm_medium=referral&utm_content=search
Part 3: Firefox Configuration
This part of the tutorial is a little more advanced and requires more time than simply installing a few add-ons to Firefox. As we saw, some add-ons require active management such as NoScript, whereas others are hands-free like HTTPS Everywhere. It takes a little longer to do but once the configuration is finished then it is hands free.
Covering the full extent on the different config settings on Firefox would take too long for this blog post, however the tutorial linked below is a good guide to different settings that should be turned off or on:
https://chrisx.xyz/blog/yet-another-firefox-hardening-guide/#disable-javascript-in-pdf-l1
Conclusion:
This article covered many add-ons and provided links to different tools and allow people to do their own research on what they want to implement. Without a doubt browser security is important when handling cryptocurrencies on a centralized exchanged or on add-ons such as MetaMask. As more people start using cryptocurrencies the more that people will hopefully understand that the internet is not built to be secure. It is open-ended and needs to be closed off. Browser hardening is one of the first steps in this process and a is beginner friendly way to introduce this topic. In future articles additional cybersecurity tools may be covered.
Bibliography:
https://restoreprivacy.com/firefox-privacy/
https://www.privacytools.io/
https://www.eff.org/
https://coveryourtracks.eff.org/